If you type “Target Breach” into a search engine you will get a plethora of articles discussing why, how, and what we should do about it. I can’t fight my inclination to chime in on the discussion. What should our takeaways be? I’ve narrowed it down to three.
1) What was really stolen? Credentials!
How did the bad guys access Target’s extensive point of sale system? Evidence indicates that they harvested stolen credentials from an employee of Target’s HVAC company. Let me say that another way… The heating and a/c company had an account with basic access to Target’s IT systems (similar to a NetID in SB lingo) and using the stolen password they stole millions of credit cards. Is that surprising? Not really. This type of attack is called “privilege escalation.” Once someone has basic rights to a system, they can then start looking for holes and hop around an internal network until they find another step higher on the staircase to heaven, or in this case, credit card number bliss.
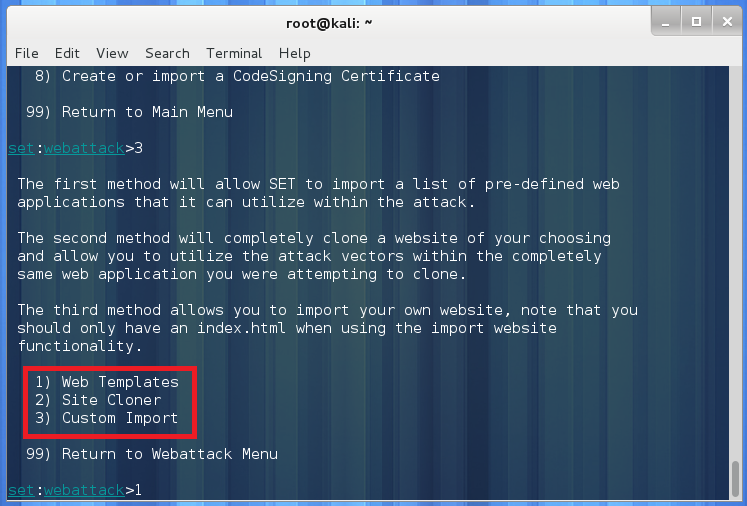
It may also sound intimidating to think that they “harvested” his credentials. All that really means is that they probably sent the HVAC company a phishing email with a link to a phony website. We get those almost every day. Most people would be surprised to learn that there is step by step documentation on how to to launch this type of an attack. You don’t have to be an experienced hacker to do it. In fact, the easiest way to do so is using something called the “Social Engineering Toolkit.” It is literally a menu driven program that can be used to create a phishing website and send out e-mails to get someone to visit your fake site. No HTML or programming skills needed. Notice the screenshots below to get an idea on what it takes to setup a basic phishing website.
Hacker says to himself, “Hmmmmm, what should I do today. Let’s go with social engineering! That is clearly choice number 1!”
“Phishing…no not right now. Mass Mailer…nah. Ooh let’s see what is behind door number 2, Website Attack Vectors!”
“If there is one thing I’m missing it’s someone else’s credentials! I will choose credential harvester,” logically states the credential starved hacker.
“I love how this tool has the ability to clone an existing site. However, I think I will take a quick look at the built-in templates,” thinks the efficient hacker.
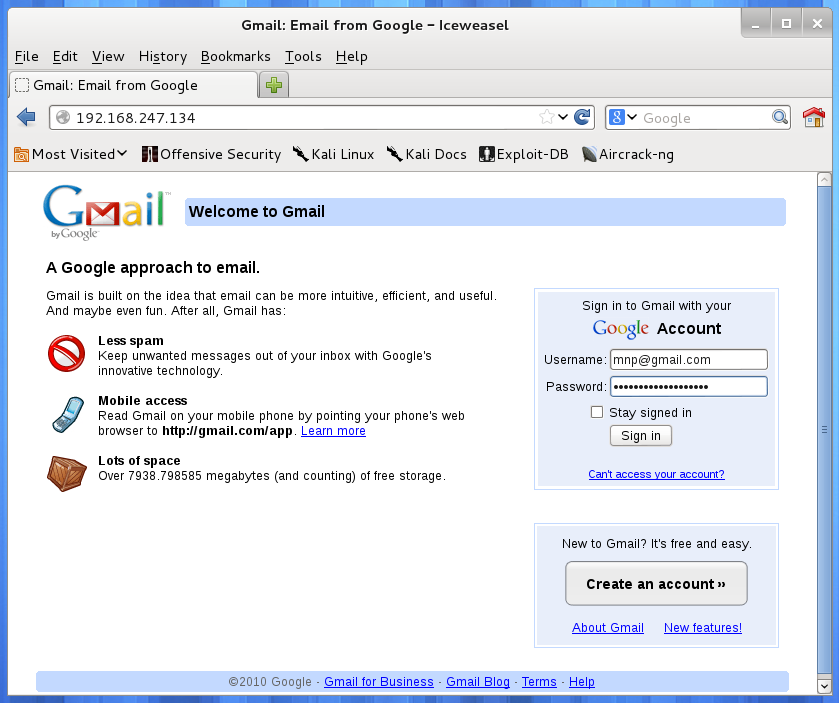
“YES! There is an existing template for Gmail! This is shaping up to be a wonderful day. As it turns out, many of the organizations I am interested in uses Gmail. I will pick choice number 2,” concludes the hacker.
“Hello trusting academic professional. Please click on this link and login to Gmail,” snickers the excited hacker as he sends out his email. “I sure hope they don’t notice the strange address in the address bar…”
Behind the scenes, this is what our hacker is seeing…credentials successfully harvested!
Admittedly, this is not the whole story especially not when it comes to what happened in Target’s case, but this should give you an idea of how accessible launching a phishing campaign is to the black, white and grey hat hacker community.
The lesson here is simply to use strong passwords, change them regularly and use discernment when reading emails and clicking on links.
2) Regulatory compliance (PCI) is a MINIMUM standard.
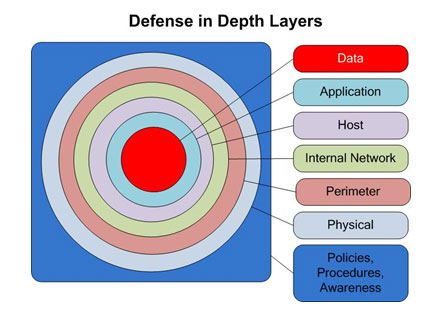
Target is PCI compliant. In this case, regulatory compliance did not protect the data it was intended to protect. Does that mean PCI is worthless? Not by a long shot. PCI is a minimum standard. No standard will ever successfully prevent every possible breach. I still believe it is a valuable baseline and compliance will prevent a wide range of credit card fraud. However, being PCI compliant is not enough. For example, regulatory compliance will never be able to secure the human element of security. All the PCI compliance in the world would not prevent someone from the janitorial staff (out of PCI scope for all intents and purposes) from giving away their credentials. With that said, layers of protection are critical. Never should we assume that data is safe inside the perimeter. Defense in depth portrays important data like the core of an onion, protected by many layers along the way. Each layer can and will fail at times, but they would all have to fail for a breach to be successful.
3) Shop with a Credit Card
I hate using credit cards because I, ahem, “forget” to pay them in full. For that reason I started using my debit card everywhere, including random gas pumps, 7-11’s, obscure websites and even at Target and Michaels. I’m exaggerating slightly, but the point is that if the money is taken from your bank account it’s harder to get it back. Sometimes it’s impossible. Use a credit card and take advantage of the fraud protection Visa, MasterCard and others offer. At worst you will lose $50.00 if you report fraudulent charges promptly and most credit cards refund your account in full immediately upon receiving a report.
In summary, be aware of phishing attempts regardless of how small or large your role in an organization is. Learn about regulatory compliance that affects your area of expertise and don’t just meet the standard, exceed it. Finally, when spending your hard-earned money, spend someone else’s first by means of a credit card and then pay them off in full as fast as you spend.
We are a target. We can’t change that. However, we can determine how easy of a target we are willing to be.
Do you think there are other important lessons to be learned from the Target incident? Post your comments below!