As I dive deeper into the world of cyber, I tend to quote my father about once a week, “If I knew then the things I know now!” I have been trying to share some of these worst kept secrets from time to time and here’s another one. A single tool that I can’t believe I lived without for so many years.
The tool’s name is…drumroll please…
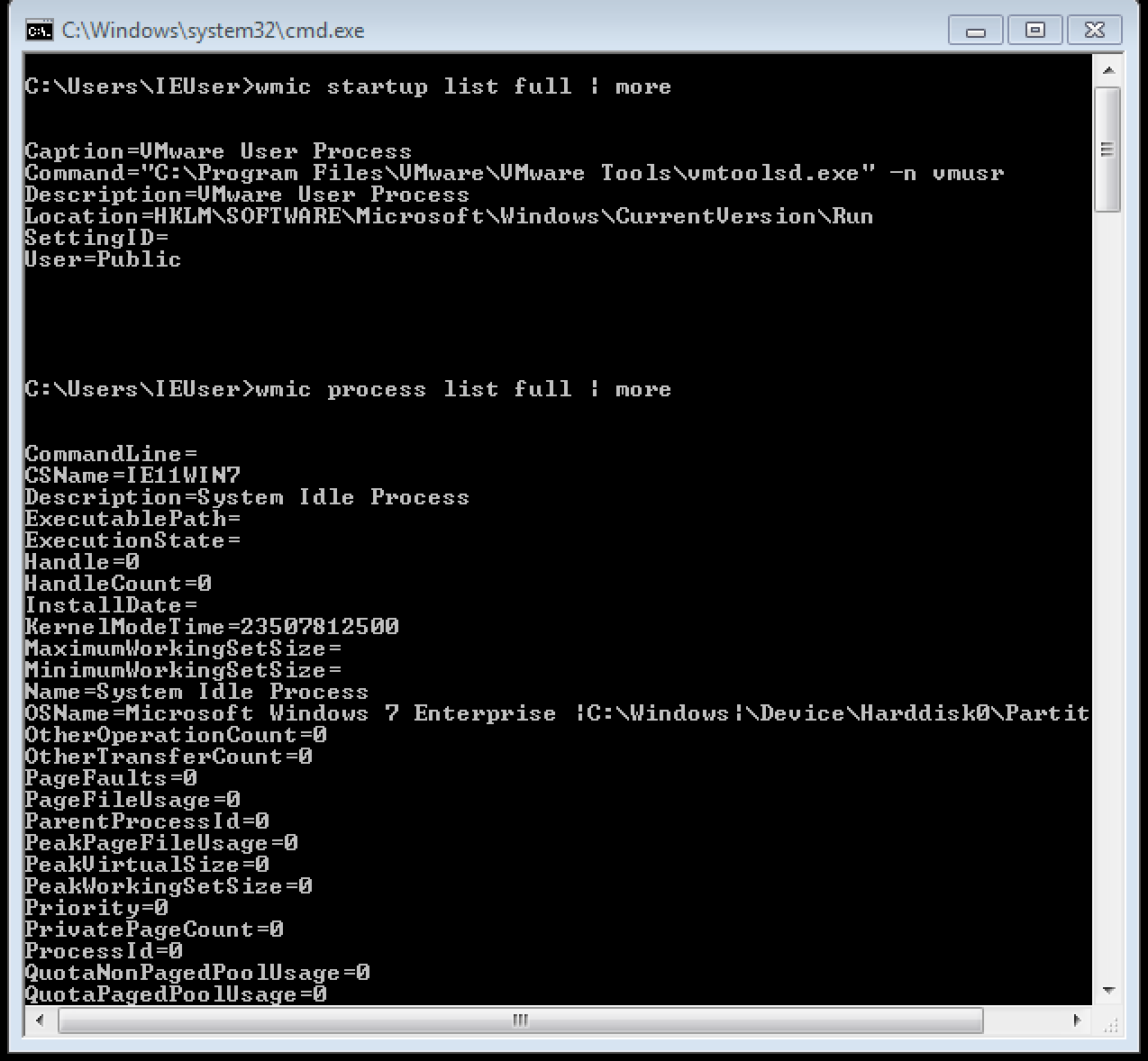
WMIC.
If you already know about it, awesome. You’re legit. If not, learn about it right now and start to think about how you can use it. WMIC can query just about anything about your system and tell you what’s really going on.
Two commands in particular you should commit to memory right now:
wmic startup list full | more will show you every process that runs at startup. Hugely valuable for finding evil processes or even just troubleshooting performance.
wmic process list full | more is like task manager on steroids. And this command is a kernel-level command, so evil processes have to work harder to hide from it. There is one portion of this output that is just priceless. Look closely and notice the line “ParentProcessID.” It actually identities what process spawned each subsequent process. So, if you are suspicious about a particular process and find out that the parent process id is iexplore.exe, you might be on to something. Or maybe you find that the parent process id is explorer.exe, then it’s probably something you double clicked…DOH!
And YES, wmic can be used to query computers across the wire, just use the /node:%computername% switch. Wmic is extremely powerful and its usefulness is only limited by your imagination. But step one is knowing it exists! Now you can proceed to step 2.
The SANS Windows Commandline Cheat Sheet gives some more detail about this command and several others. Be sure to check it out.
What other commands do you know about that are under utilized or desperately in need of some more attention? Let us know in the comments below.
Thanks for reading and don’t forget to subscribe.