I recently completed the SANS SEC401 Security Essentials Bootcamp course via an online on-demand webcast. If taken in person, this course runs 9 AM to 7 PM for six days…hence the “bootcamp” label. With the on-demand format, you have the added privilege of viewing the lecture content at your own pace over a four month period.
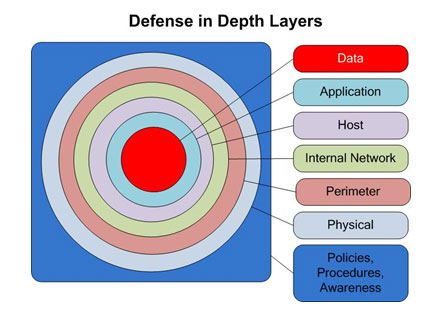
If I can summarize the course in one word it would be, “AWESOME.” The writer and instructor of the course is Dr. Eric Cole, a fellow of the SANS Institute. His enthusiasm is contagious and he made approximately 50 hours of lecture content fly by in what felt like a mere 49 hours. That is no simple feat considering the content. Each day is dedicated to a particular topic: Day 1: Networking Concepts, Day 2: Defense In-Depth, Day 3: Internet Security Technologies, Day 4: Secure Communications, Day 5: Windows Security, Day 6: Unix/Linux Security. Oh, and there is a corresponding book for each day…
I read every word and went the extra measure of creating an index for all 6 volumes, which SANS intentionally neglects to include to encourage “Learning.” I followed the advise posted by this fellow SANS trainee so I won’t bother going into detail. My index looks eerily similar to his and I found his blog posting very useful. In total it is 28 pages long.
What I especially loved about this course is that Dr. Cole added so much real world context to the material. The course differs from the “textbook” model of teaching, and as far as I’m concerned, this should be a requirement for all security courses. Textbook and real world are often misaligned. The content addressed these challenges head on. On the other hand, examples were provided of when textbook recommendations have been ignored and at what cost. For example, he talked about a scenario where an adversary breached a very large network. One of the well meaning administrators sent a message over email in reference to cleaning up the breach. Oops…they never had a chance because the adversary read the email and inflicted as much damage as possible by Monday. This highlights the importance of out of band communication in the event of an incident.
There was also tons of hands on labs and practical content. I spent the time doing every lab and had the opportunity to play with tools like tcpdump and even messed around with stego crypto. It was kind of fun hiding a secret message to my wife within a jpg picture of our kids. Hands on training is a simple, but powerful learning technique and SANS makes good use of this as part of their curriculum.
Compared to the CISSP content, which I consumed 6+ months ago by means of a self-study program, I found there to be some overlap. More often than not, the SANS training looked at hands-on topics more granularly, but areas of theory were covered in more detail within the CISSP courseware. For example, the Bell-Lapadula model was briefly mentioned in SEC401, but explained in further detail by the CISSP. Overall, I am happy in the order that I pursued these credentials, but they could have been tackled in reverse order just the same!
This class truly was a bootcamp and for that reason I did appreciate the ability to go through the material at my own pace. In some regards, though, I think doing so is prolonging the pain, er, I mean, extending the fun. There is something to be said for battening down the hatches and going off-grid for 6 long days versus trying to steal 6 long days from your normal schedule. Some other courses which are more lab intensive and collaborative, would not be as good if taken in this format.
SANS offers endless training opportunities and there is a case to be made for all IT employees to take some of their training. For example, they have an entire course that focuses on Windows Security. There’s another that focuses on Unix Security. Secure Web Development? They got that. Let’s not forget Network Security… The list goes on and on. These courses are not just for security analysts. They are for IT professionals who want to accomplish their job in a secure manner and I highly recommend them to all IT administrators. Perhaps one person from each department could attend one SANS course per year? Wishful thinking perhaps, but it would be a great investment and in line with our core values here at DoIT.
I will be taking the associated GIAC GSEC exam within the next week for the sake of putting a rubber stamp on this experience. However, it’s really all about the journey, not the destination!
Some food for thought from the course:
1) Prevention is ideal. Detection is a must.
2) What is the risk? Is it the highest priority risk? Is it the most cost effective way to mitigate the risk?
3) TCP/IP and TCPDUMP Cheat Sheet
4) SANS Windows Tools and Scripts Download
5) Baseline your systems while they are healthy by, at a minimum, documenting running processes, listening ports, existing users (especially admin and root level access UID 0) and admin group membership.
Rating: Excellent – I’d pay my own way … okay, not really, but that’s how much I liked it.
Thanks for reading and don’t forget to subscribe!


 I recently became aware of a couple of scams that can significantly hurt your wallet because the end result is a bunch of unauthorized, but legitimate (from the phone company’s perspective) charges on your cell phone bill. The prevention of these scams is extremely simple and non-technical.
I recently became aware of a couple of scams that can significantly hurt your wallet because the end result is a bunch of unauthorized, but legitimate (from the phone company’s perspective) charges on your cell phone bill. The prevention of these scams is extremely simple and non-technical.




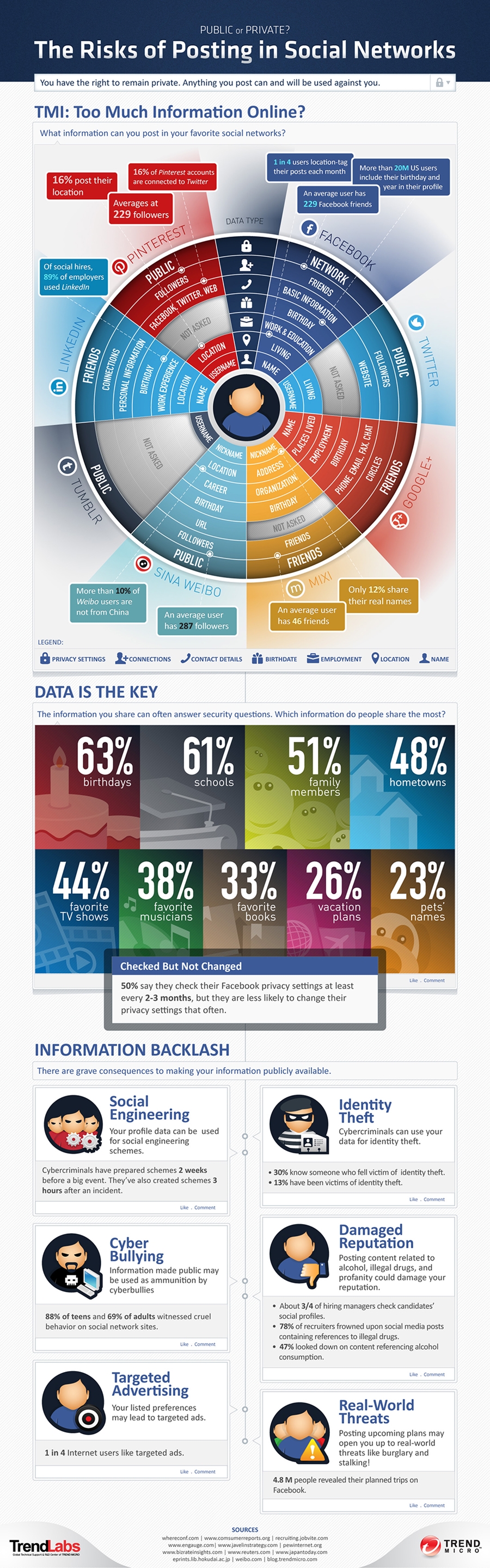 Thank you for tuning in to this public service announcement (PSA) regarding too much information (TMI).
Thank you for tuning in to this public service announcement (PSA) regarding too much information (TMI).